Testing Firewall Rules With Nmap
Testing Firewall Rules With Nmap. While mapping out firewall rules can be valuable, bypassing rules is often the primary goal. Individual techniques each have a low probability of success, so try as many different methods as possible.
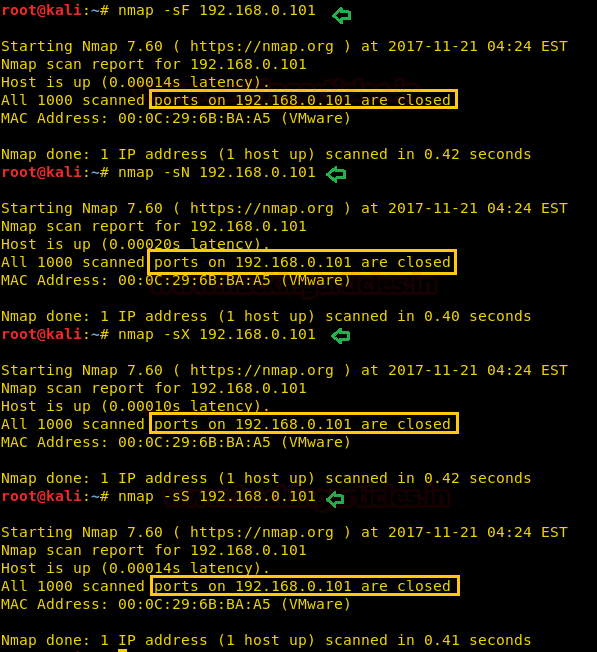
Detecting a Firewall Prev Next Block and Slow Nmap with Firewalls One of the best defensive measures against scanning is a well-configured firewall.
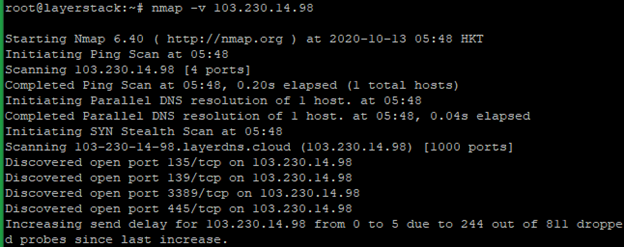
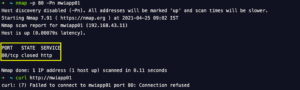
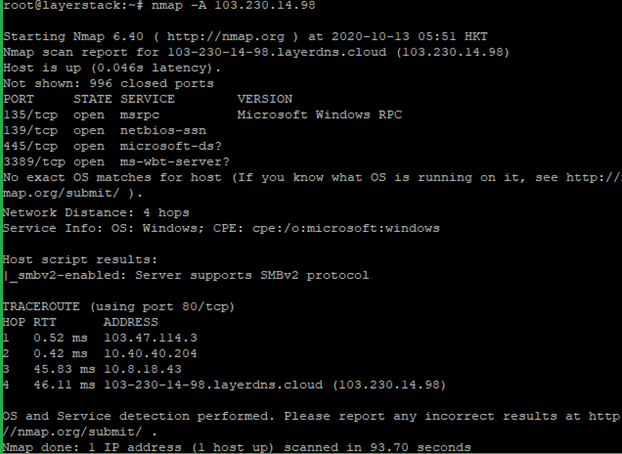
This tutorial will demonstrate how nmap can be used for firewall penetration testing to evaluate and improve the security of your network.
A tutorial is beyond the scope of this reference guide, which only lists the relevant options and describes what they do. -f (fragment packets); --mtu (using the specified MTU) Testing firewall and IDS rules is a regular part of penetration testing or security auditing. Setting back a firewall for your it and infrastructure is a great way to provide some basis security by your billing. Rather than simply obfuscate the network configuration, as some techniques described later do, well-configured firewalls can effectively block many avenues of attack.